We began with the repository https://github.com/crux-bphc/ctf-git-lost, where the main branch didn’t reveal much initially. However, the commit message’s hint, “Empty start, but secrets lie beneath,” pushed us to dig deeper.
Clues in the Activity View
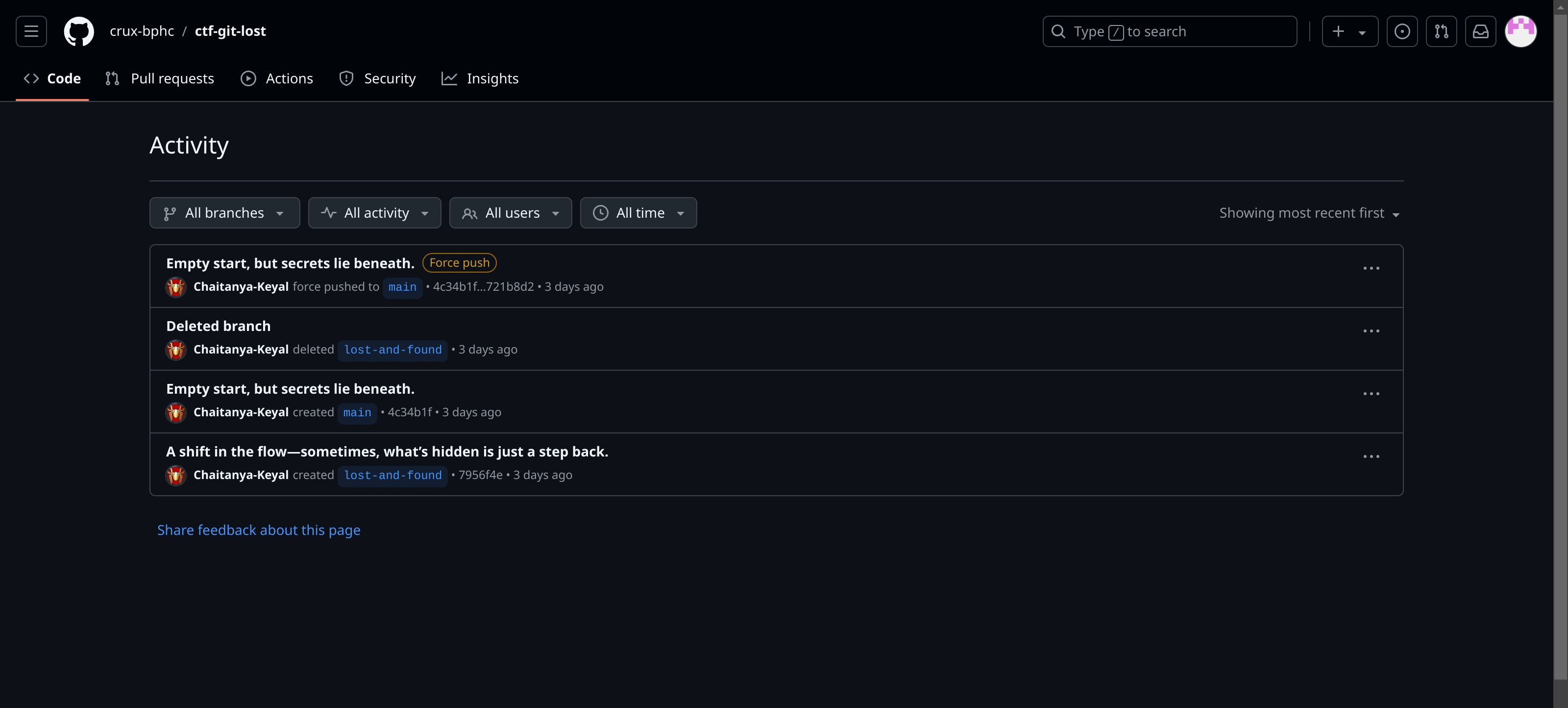
Examining the repository’s activity, we noticed the creation and deletion of a branch named lost-and-found. This looked suspicious, so we explored the commit changes and found an encrypted text.
Changes in the Commit Message
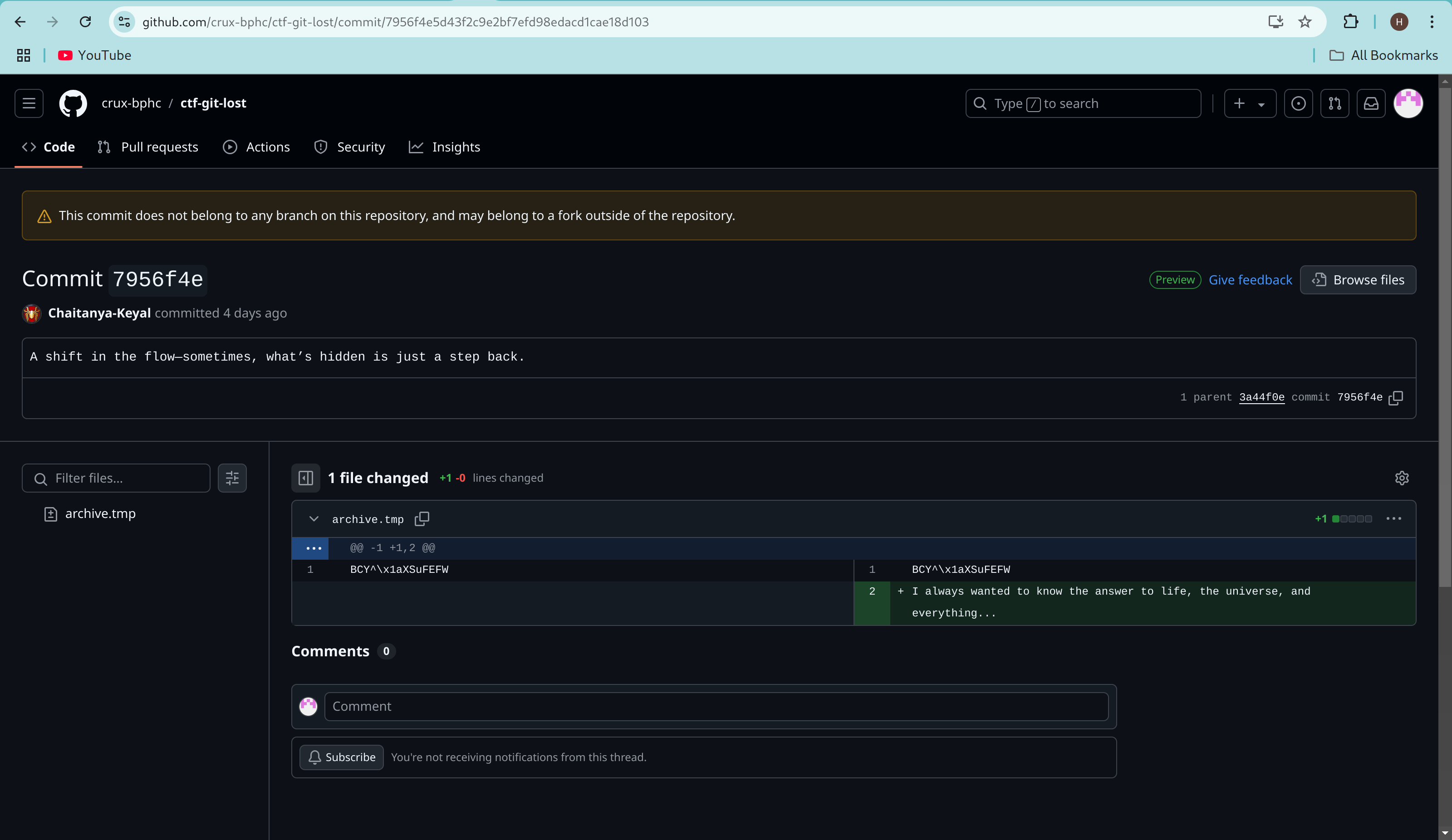
Deciphering this encrypted content seemed essential for unlocking the hidden secrets in the repository.
Discovering the Dangling Repo
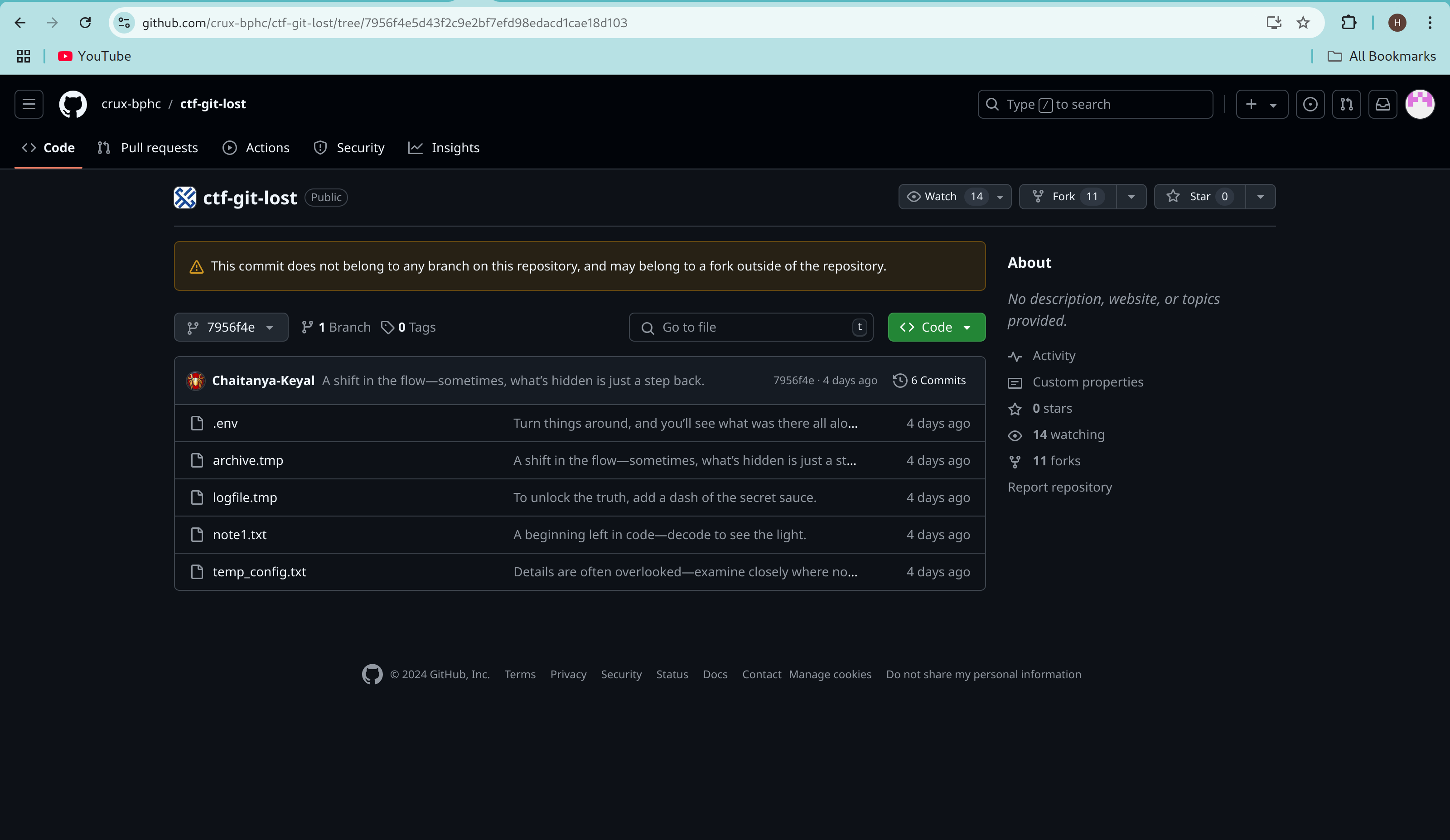
Changing the commit view to a tree structure led us to several dangling files, providing potential sources for the key elements of the challenge.
Decoding the Secrets in Each File
Here’s the process I followed for each file in the repository:
-
.env: UsingROT13, I decryptedvcc3q_zl_to revealipp3d_my_. -
archive.tmp: Recognizing it as an XOR cipher and using “the answer to life, the universe, and everything” (hint: 42) as the key, I decryptedBCY^\x1aXSuFEFWtohist0ry_lol. -
note1.txt: The base64-encoded textY3J1WGlwaGVye3kwdV8Kdecoded tocruXipher{y0u_. -
temp_config.txt: I realized the file contained binary representations (spaces as0and tabs as1). Using a Python script, I decoded it toju5t_unz.
def decode_whitespace_from_file(filename):
# Define the binary translation for spaces and tabs
binary_translation = {' ': '0', '\t': '1'}
# Read the file content
with open(filename, 'r') as file:
lines = file.readlines()
# Convert each line to binary, then concatenate all binary strings
binary_string = ''.join(
''.join(binary_translation[char] for char in line if char in binary_translation)
for line in lines
)
# Convert binary to ASCII text (each 8 bits -> 1 character)
text = ''.join(chr(int(binary_string[i:i+8], 2)) for i in range(0, len(binary_string), 8))
return text
# Usage example
filename = 'temp_config.txt'
decoded_text = decode_whitespace_from_file(filename)
print("Decoded Text:", decoded_text)
logfile.tmp: The final piece was AES-encrypted textU2FsdGVkX1+NHOZKkOJXRLcJxUjzvblDEgXOijcs8Jk=, which required a key I couldn’t initially determine.
Discovering New Updates in the Repo
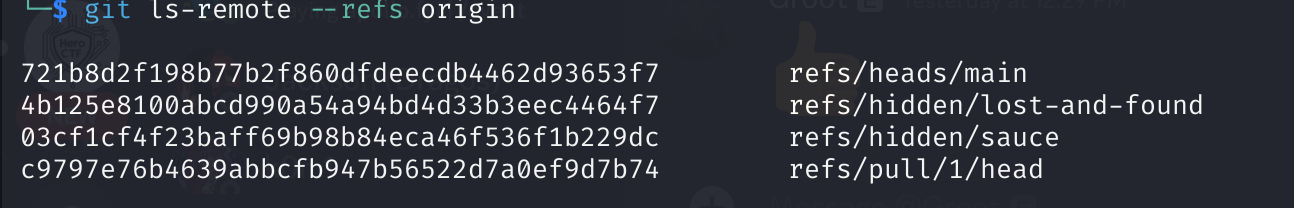
Using git ls-remote --refs origin, I found the newly hidden repo sauce. Browsing the tree structure didn’t yield results, leading me to try accessing the blob directly.
Accessing the Blob Object
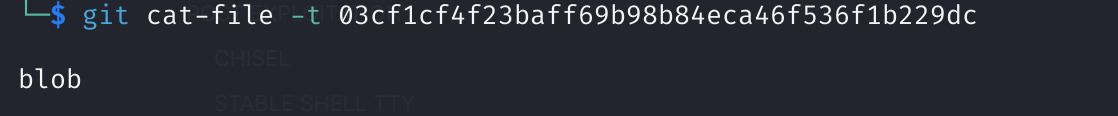
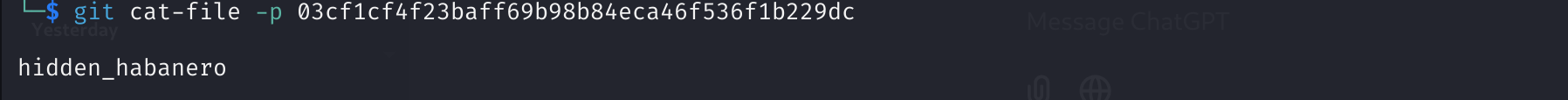
Opening the blob object gave me the final key needed for decryption!
Using the Key to Decrypt the AES Cipher
With this decryption key, I unlocked logfile.tmp, revealing the challenge’s final flag:
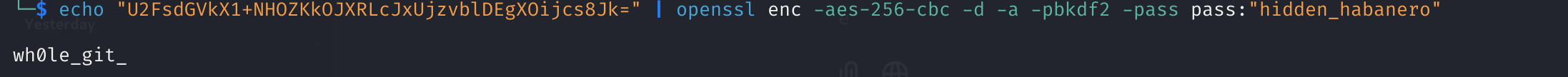
The Final Flag
cruXipher{y0u_ju5t_unzipp3d_my_wh0le_git_hist0ry_lol} 🎉
Join NOVA! 🌌
As a proud member of team NOVA (Rank 16), I invite anyone interested to join our journey. If you’re up for the challenge, just DM 5pideyy. Thanks for reading and happy hacking!